Third Party Risk Management
Alliance TPRM
Securing your entire supply chain
Assess third party risks, manage vendor networks and safeguard your business against potential vulnerabilities.
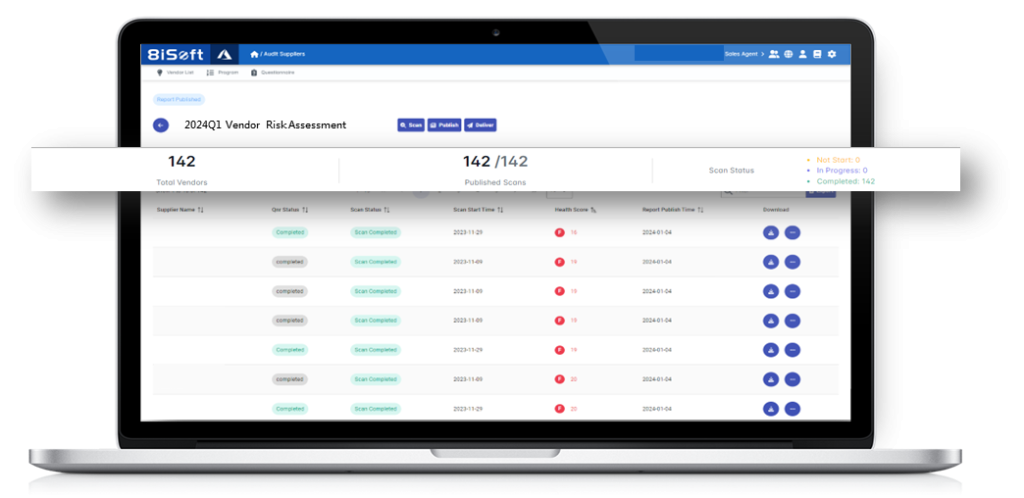


Unified Vendor Lifecycle Management Platform
Alliance Third Party Risk Management (TPRM) helps your business manage an organizations’ greatest risks— Vendors. Our platform excels in identifying, assessing, and managing information security risks associated with third-party suppliers, ensuring compliance with ESG governance standards. Streamline your supply chain risk management process with our user-friendly, automated features:
- Automated Risk Assessments for all suppliers and vendors
- Comprehensive Dashboard for continuous tracking of third party vendors
- Easily manage all vendor documents in one centralized platform
- Enhanced vendor remediation guidance with YODA AI
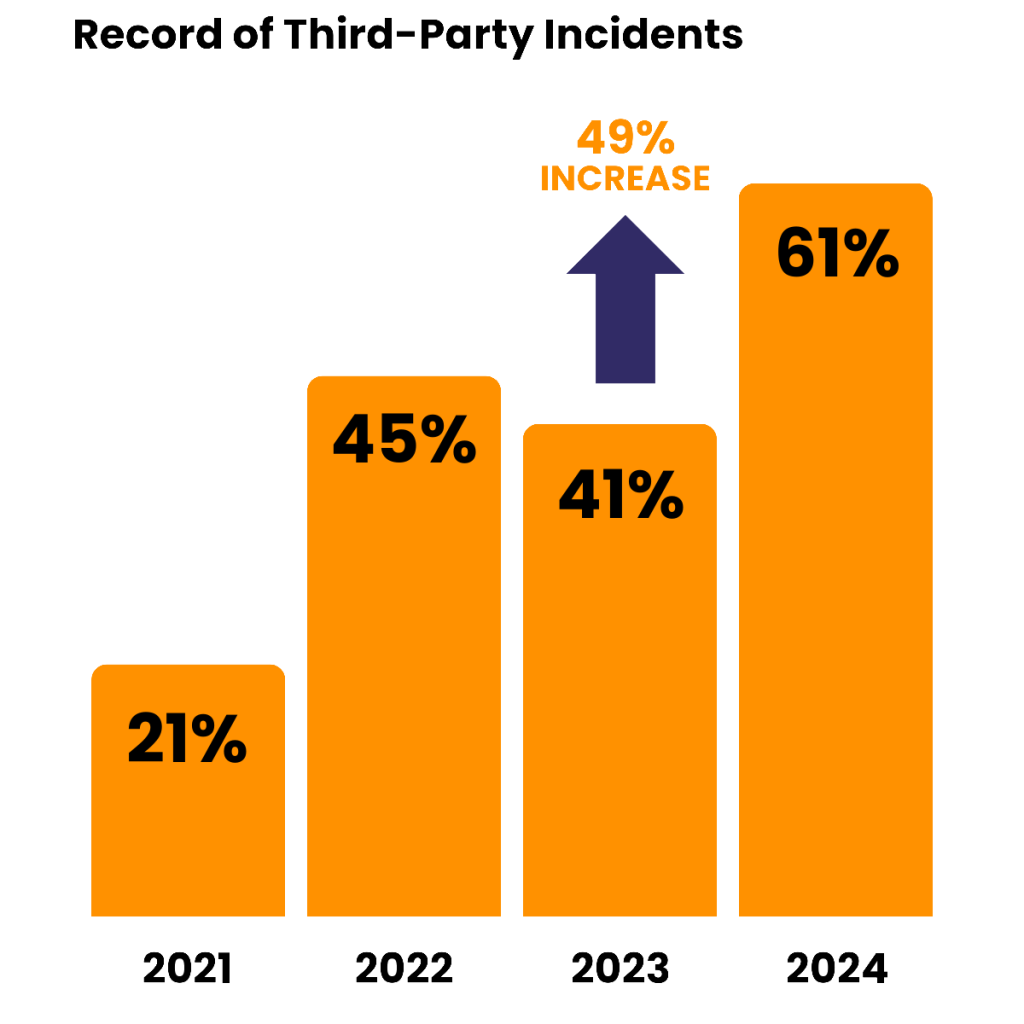

A 2024 study found that 61% of companies faced significant third party data breaches in the past year, highlighting the urgent need for robust Third Party Risk Management solutions.
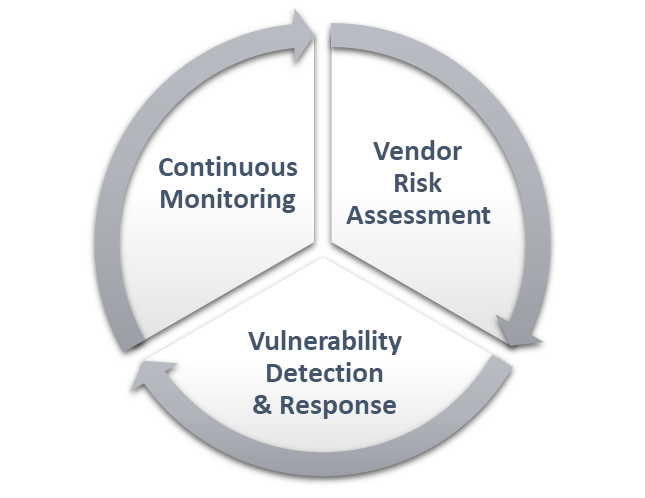
Automation, Collaboration, Continuous Monitoring
Monitor supplier risks at every stage of the vendor management lifecycle—procurement, reassessment, and decommissioning. Our third-party risk management team adopts a customized approach aligned with your enterprise’s risk tolerance and program maturity. We combine workflow automation with objective data for strategic decision-making.

Step 1. Setup/Initiate
Invite suppliers to join the platform and establish your list of third parties.


Step 2. Review
Centrally review supplier documents (risk assessments, certifications, questionnaires and more), all on the platform for easy auditing.


Step 3. Analyze
Get a complete grasp of your supplier risks with a single dashboard that consolidates and analyzes evidence.


Step 4. Monitor
Closely monitor changes in your supplier portfolio and instantly understand their impact on risk tolerance.
Spotlight Features
Navigating Every Risk, Crafting a Resilient Supply Chain
Security Assessment and Management
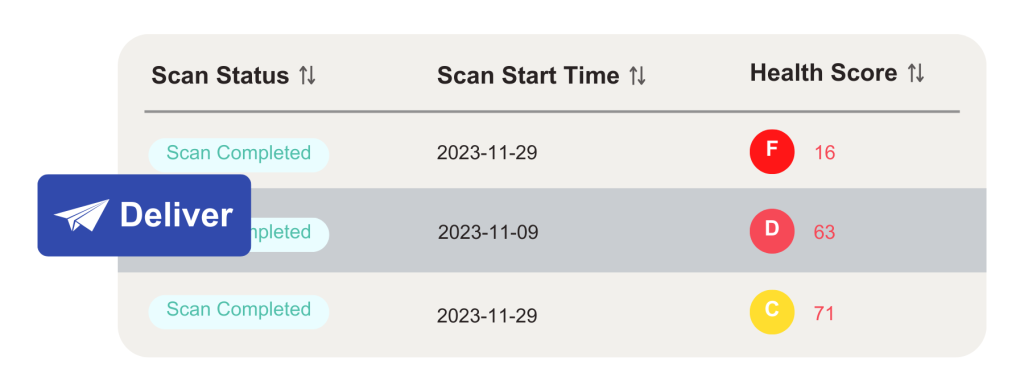

- Holistic Risk Scoring : We employ CVSS and CVE standards to evaluate vulnerabilities for an unbiased, thorough, and accurate/precise security assessment of our suppliers.
- Streamlined Management: Simplify processes with a single click to generate supplier risk assessment reports. Access data on 5,500+ suppliers for effective and efficient risk management decisions
- Empower Decision-Making: Leverage data-driven insights to monitor supplier security and generate three key scores for a clear perspective on the safety of your partnerships.
Integrating Management and Collaboration
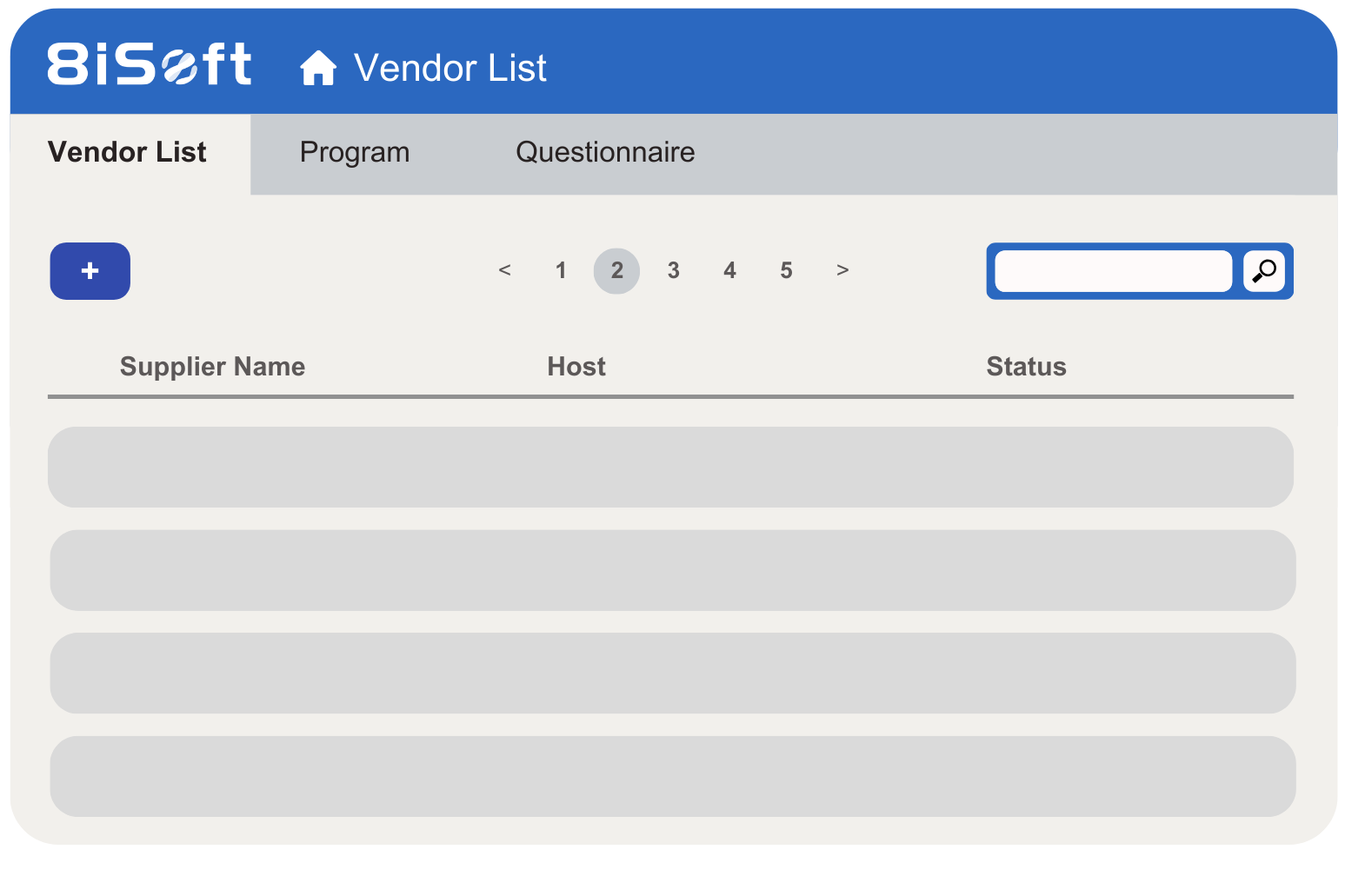

- Unified Supplier Information Management: Seamlessly merge basic and host information to establish a transparent foundation for managing supplier risks.
- Enhanced Data Visibility:Automatically collect supplier data to enhance TPRM visibility, encouraging easy collaboration for addressing future challenges.
- Centralized Management: Unify supplier risk management by integrating all supplier information for a clear and transparent process.
Intelligent Monitoring and Insight
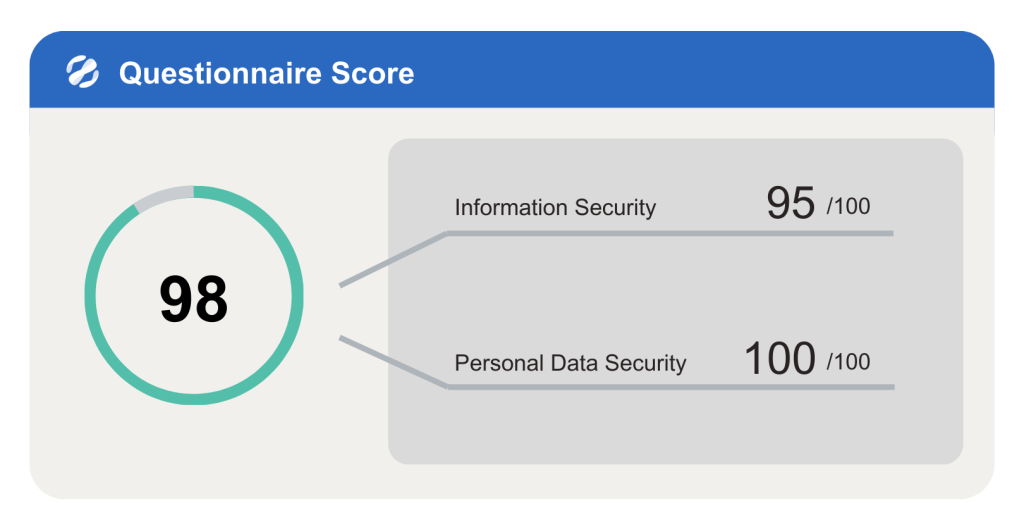

- Continuous Risk Monitoring: Keep an eye on risks using real-time dark web intelligence to ensure quick identification and response.
- Smart Control: Utilize predefined indicators and custom parameters to shape a scoring system, delivering a comprehensive and intuitive security report that eliminates blind decision-making.
- Human Risk Management (HRM): Conduct behavioral risk analysis, provide security awareness training, and support suppliers in improving awareness of human factors.
Supplier Collaboration and Continuous Monitoring
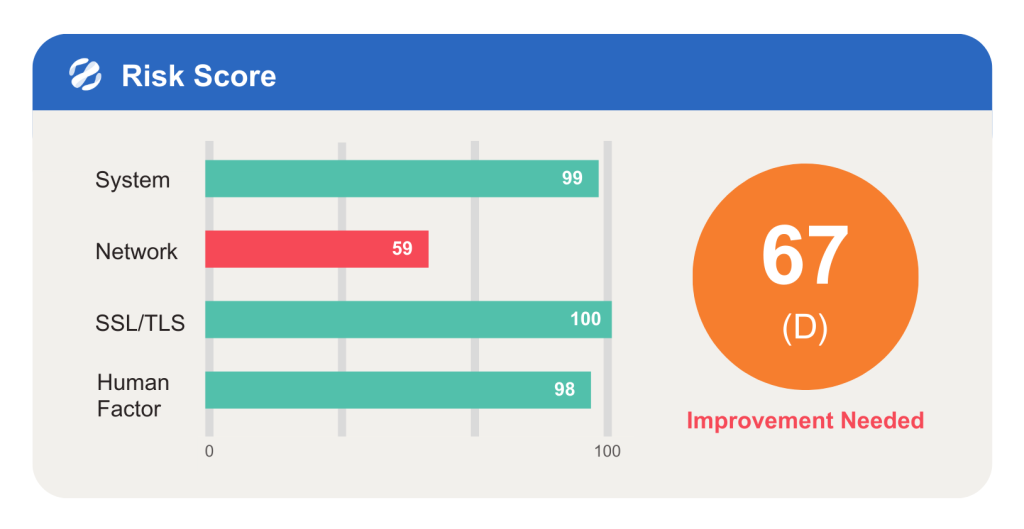

- Collaboration-Boost Platform: A platform for businesses and suppliers to facilitate joint vulnerability management that fosters effective communication and cooperation.
- Compliance Monitoring Support: Ensure continuous visibility and insight. Integrate external data flows for risk assessments. Synchronize Third-Party Risk Management (TPRM) data with GRC and reporting tools via APIs to ensure suppliers comply with regulations and standards.
- AI-Powered Efficiency: Utilize AI to analyze data, deliver more accurate risk assessments, and help businesses establish a robust supplier collaboration ecosystem, achieving automated supplier data collection and integration.
Experience the Difference
Alliance is suitable for vendors in the following categories:

Financial Platform
Suppliers responsible for data flow into the company’s systems.


Payroll Service
Suppliers holding information about clients/employees.


Law Firms
Suppliers holding sensitive information about the company.


Key Technology Providers
Suppliers storing design data and detailed product information.
Learn More about Third Party Risk Management
Ready to Start?
Collaborate Now to Achieve a Zero-Risk Supply Chain
